Secure Boot Certificate¶
NOTE: We have started using a new key for package signatures and kernel module signing. As a user you might encounter packages and kernel modules signed either with the legacy pldp key or the new soliddriver key. In some instances you might need to load both UEFI certificates into your machines key database
The kernel module signatures are used when running SUSE Linux Enterprise in UEFI Secure Boot environment. To ensure the integrity of the running kernel, the kernel will only load modules signed with trusted keys.
The key is considered trusted once the user loads the corresponding Secure Boot certificate into a UEFI key database
UEFI Key Database (key db)¶
The recommended way to enroll a trusted key into the system is to load the certificate into the UEFI firmwares key db. Reference your system documentation or contact your system manufacture for options to add certificates to the key db. Find the SolidDriver certificate here:
Legacy Certificate pldp-UEFI-SIGN-Certificate.crt
New Certificate soliddriver-UEFI-SIGN-Certificate.crt
If there is no user option to maintain keys in the UEFI key db, the next option is to use the Machine Owner Keys database described in the following section.
Machine Owner Keys (MOK) database.¶
For systems that do not allow user (system admin) control over the UEFI key database, the Machine Owner Key (MOK) database option can be used. Note: it’s recommended to use the key db if at all possible
The certificate can be enrolled into the MOK by installing the following package:
Legacy Certificate pldp-UEFI-SIGN-Certificate-1.1-1.1.x86_64.rpm
New Certificate SolidDriver-UEFI-SIGN-Certificate-1.0-2.1.noarch.rpm
This package contains the UEFI Secure Boot certificate used to sign modules built in SUSE’s Partner Linux Driver Program. It will install the certificate under /etc/uefi/certs as well as prepare it to be enrolled into the MOK database of the firmware.
Note: The kernel will only load the MOK database when the system is booted in UEFI Secure Boot mode. When not in Secure Boot mode, SolidDriver kernel modules will load, but since the module is signed with a key unknown to the kernel, the kernel will emit a “module verification failed” message and a kernel taint will occur. To prevent that taint, the certificate must be loaded into the UEFI key db manually using the firmware UI.
Installation¶
Install the package using zypper or YaST as you would any other rpm package. After package installation, the system must be rebooted to complete the process of enrolling the key into the UEFI MOK database. At reboot the following UEFI prompt will be displayed on the system console:
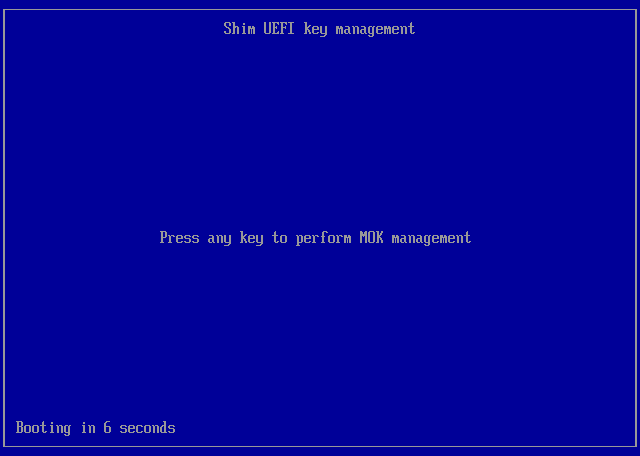
Initial Screen with Timeout¶
This prompt will timeout after 10 seconds and reboot without enrolling the key. Press any key to enter the enrollment process.
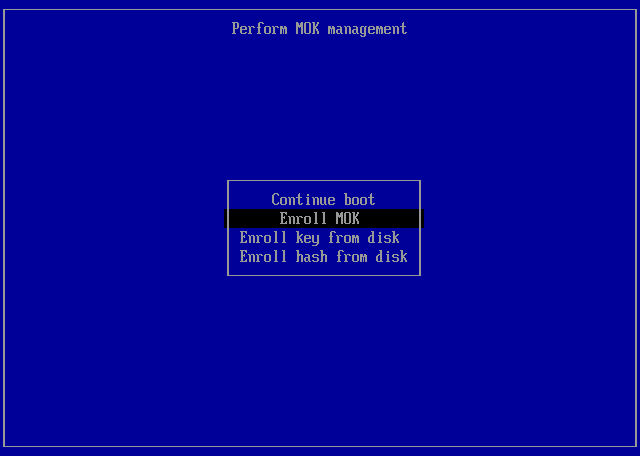
Initial Menu¶
Select Enroll MOK in the menu
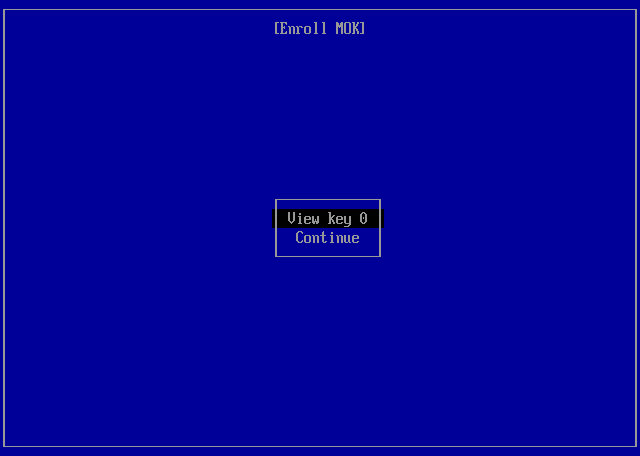
Select View Key 0¶
Select View Key 0 to view the details of the certificate to be enrolled
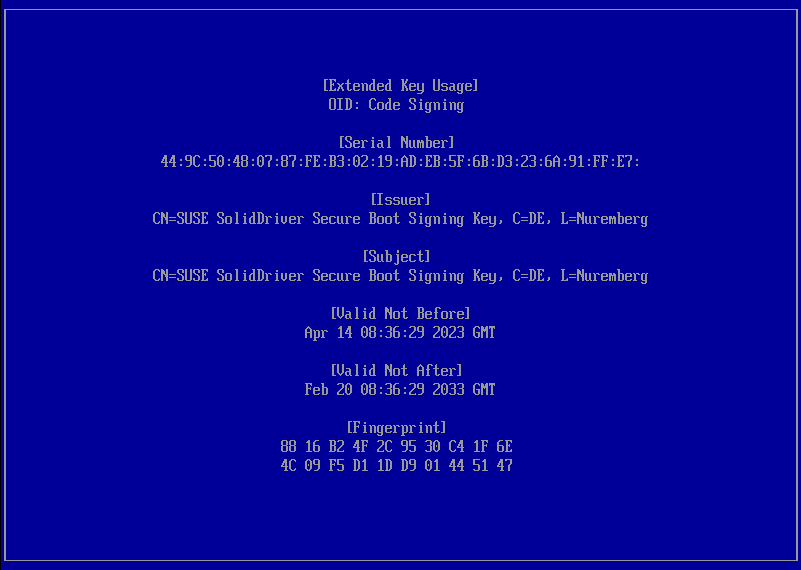
Key Details¶
Verify the key details and press any key to continue
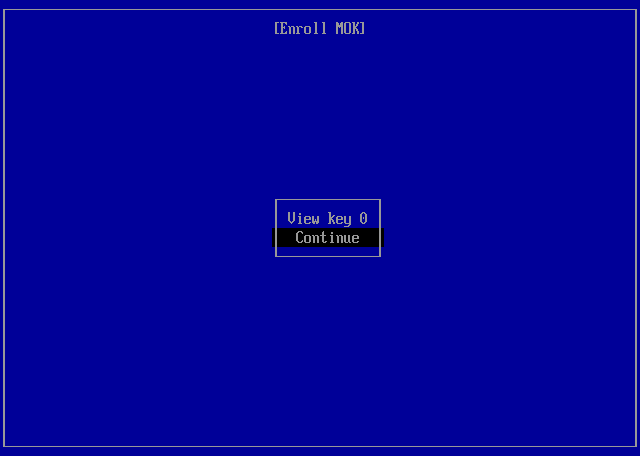
Enroll Key¶
When ready to enroll the key, select Continue
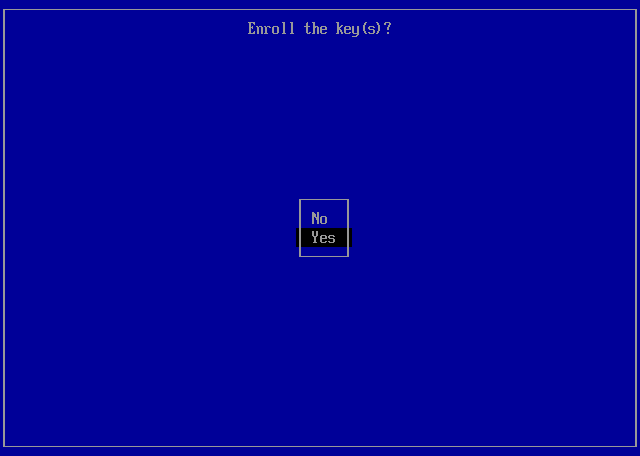
Confirm¶
Select Yes to confirm enrollment of the key

Enter Password¶
Enter the system’s root password to authorize the enrollment.
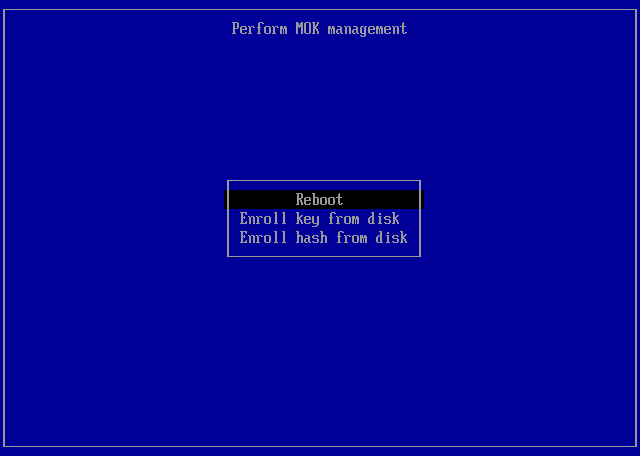
Reboot¶
Select Reboot to reboot the system.
The key is now enrolled. To verify this, check the kernel messages after reboot:
# dmesg | grep integrity
[ 1.272726] integrity: Platform Keyring initialized
[ 2.196452] integrity: Loading X.509 certificate: UEFI:db
[ 2.276342] integrity: Loaded X.509 cert 'SUSE Linux Enterprise Secure Boot CA: ecab0d42c456cf770436b973993862965e87262f'
[ 2.277281] integrity: Loading X.509 certificate: UEFI:MokListRT (MOKvar table)
[ 2.277612] integrity: Loaded X.509 cert 'SUSE Linux Enterprise Secure Boot CA: ecab0d42c456cf770436b973993862965e87262f'
[ 2.277614] integrity: Loading X.509 certificate: UEFI:MokListRT (MOKvar table)
[ 2.277926] integrity: Loaded X.509 cert 'SUSE Linux Products GmbH: PLDP Secure Boot Signing Key: ced5e22b63eee758a2e16663a4c2c35bbb54e54f'
[ 2.277928] integrity: Loading X.509 certificate: UEFI:MokListRT (MOKvar table)
[ 2.278915] integrity: Loaded X.509 cert 'SUSE SolidDriver Secure Boot Signing Key: a2a49204cba8e6dd5f2507b821cb50a9d0841db5'
The SUSE SolidDriver Secure Boot Signing Key is in the list of loaded certs. If not, then the key was not enrolled properly.
Using mokutil to list enrolled keys
One can also verify that the certificate is loaded in the MOK database
by using the mokutil command:
# mokutil --list-enrolled
[key 3]
SHA1 Fingerprint: 88:16:b2:4f:2c:95:30:c4:1f:6e:4c:09:f5:d1:1d:d9:01:44:51:47
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
44:9c:50:48:07:87:fe:b3:02:19:ad:eb:5f:6b:d3:23:6a:91:ff:e7
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=SUSE SolidDriver Secure Boot Signing Key, C=DE, L=Nuremberg, O=SUSE Software Solutions Germany GmbH, OU=SolidDriver Team/emailAddress=soliddriver@suse.com
Validity
Not Before: Apr 14 08:36:29 2023 GMT
Not After : Feb 20 08:36:29 2033 GMT
Subject: CN=SUSE SolidDriver Secure Boot Signing Key, C=DE, L=Nuremberg, O=SUSE Software Solutions Germany GmbH, OU=SolidDriver Team/emailAddress=soliddriver@suse.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (4096 bit)
Modulus:
00:c4:5d:ec:d4:b9:15:f3:79:fd:7f:d7:7a:43:7f:
6d:7b:b2:22:73:56:fa:69:39:b0:60:88:fd:55:2f:
af:e8:2d:78:60:d8:18:b5:9a:e3:c2:71:7a:66:72:
c5:54:59:d7:7a:57:0b:01:65:7e:e7:65:f8:c1:ce:
4c:bb:b9:9b:05:a9:6b:22:43:c6:53:3d:8d:12:4e:
74:dc:49:7a:50:88:09:7b:e9:21:7f:14:08:3f:93:
eb:51:d9:22:df:aa:ac:25:71:13:0e:dc:0e:11:67:
90:a0:56:93:be:d7:0d:18:2a:96:34:2c:ba:07:db:
80:9a:28:7d:d0:91:52:b6:80:e5:61:fe:7b:79:0f:
f7:0b:14:a0:50:7a:77:a7:04:42:e9:7d:76:42:d1:
86:fc:d4:ac:ef:f6:f1:21:99:33:8e:29:2d:6e:51:
a0:0f:a3:f2:13:50:96:f5:12:8a:3e:41:bb:7e:93:
20:4d:a1:33:eb:c2:14:2c:e9:6d:dc:fc:c0:c6:e9:
cb:e7:17:3a:ac:f9:3a:45:a8:d0:50:d5:de:cb:e6:
80:f9:48:63:35:8b:3a:b8:e0:bc:3a:ee:d8:6b:4c:
50:06:92:ed:99:f0:bf:bd:a5:7e:54:86:05:28:1a:
3c:bf:b8:36:4c:e0:17:8d:7f:2a:ec:ef:4b:3b:8f:
b2:e1:c7:d2:bf:c0:9d:d6:4c:a9:e9:ef:0b:40:b3:
68:fa:47:03:64:c3:8d:f2:29:85:cf:a3:ce:b3:ca:
4c:1e:65:36:c9:00:aa:9b:5d:51:40:5f:4c:96:2a:
3f:8c:43:bc:c6:c0:21:3a:04:97:1b:f5:0a:c0:fa:
a0:2d:50:59:65:c0:1e:1c:55:79:93:df:f7:18:e5:
23:aa:50:9f:b0:6b:f1:eb:b7:61:bc:17:c0:9a:d3:
68:c1:81:19:5b:88:38:56:7c:07:35:65:40:f6:b7:
2b:e9:17:a3:d0:5a:e0:91:65:2b:70:d4:e9:17:9c:
88:5e:0c:b4:7a:ab:32:0c:82:98:9f:5f:bd:1d:fa:
56:e0:51:f6:f5:60:d3:b1:b5:cc:67:b5:84:eb:d6:
f9:42:90:39:fd:72:51:0a:a2:fb:4b:dd:b8:36:c1:
3e:4f:34:bb:54:db:d1:15:63:32:0e:7a:76:e9:f5:
1c:c5:6a:af:1c:f8:8d:91:d4:61:db:ce:5c:15:6a:
be:4d:7a:dc:57:58:7d:f7:89:8b:df:0d:3d:42:50:
b0:70:1c:71:0e:f7:64:92:3b:92:44:97:4a:2a:a4:
a1:b2:fc:f5:6d:ba:dd:de:6d:cf:93:6f:7a:80:3b:
ee:58:84:2c:3b:ba:2e:79:1f:06:7c:d2:b5:70:5d:
10:be:87
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints: critical
CA:FALSE
X509v3 Subject Key Identifier:
A2:A4:92:04:CB:A8:E6:DD:5F:25:07:B8:21:CB:50:A9:D0:84:1D:B5
X509v3 Authority Key Identifier:
keyid:A2:A4:92:04:CB:A8:E6:DD:5F:25:07:B8:21:CB:50:A9:D0:84:1D:B5
X509v3 Key Usage: critical
Digital Signature, Certificate Sign
X509v3 Extended Key Usage:
Code Signing
Signature Algorithm: sha256WithRSAEncryption
89:5f:f9:77:1c:fd:00:e2:9c:47:e3:5d:74:d2:6c:e7:2f:f2:
55:b3:a3:a8:43:af:a8:24:39:fe:ac:61:c2:4b:19:9f:dc:a5:
35:fe:c8:7d:94:93:18:5d:d4:7c:e0:bc:af:8a:03:b6:c1:37:
e3:96:d6:9a:0d:22:f6:33:f3:3c:5d:ce:38:26:2b:67:f0:31:
d4:6a:83:96:99:01:d4:73:fb:cd:61:aa:c4:04:7c:dd:17:91:
58:09:8f:87:d2:c8:c6:96:fe:9d:98:6d:2b:42:c1:25:44:0d:
76:23:e0:b4:c3:5a:eb:9d:be:51:ab:de:fa:39:93:fd:2d:1a:
4b:eb:e5:0b:b6:17:6c:b4:b0:ef:04:ee:27:ad:3d:89:94:53:
05:c5:74:1c:3b:14:ca:a7:38:50:c6:97:59:87:4c:85:2d:d2:
62:59:2e:56:b8:cb:0e:0a:b5:de:4e:0c:5b:af:2c:22:17:de:
94:d7:40:0f:0c:56:41:df:8e:4e:e7:0a:05:f1:a1:73:1c:ab:
db:02:d1:77:c8:60:89:b1:1c:d1:cf:a2:c2:e2:8a:89:4e:1d:
24:89:32:32:a6:65:aa:b2:f9:85:ea:4e:4f:f2:da:00:38:f3:
85:19:87:7a:47:19:68:65:26:68:4d:75:73:72:76:9d:4c:58:
27:13:89:ef:2c:5b:97:ae:3f:26:60:78:15:10:fd:72:5e:25:
f6:58:53:ed:9d:25:bf:7e:a4:a2:c4:40:10:85:ae:42:29:5f:
8b:fb:58:c5:96:3a:7a:65:c8:0e:2c:c6:05:06:ba:f9:c2:45:
16:7d:48:02:86:cc:ac:7d:31:6c:d5:6d:16:dd:26:12:7b:d6:
43:e7:42:34:f2:56:0e:10:53:fb:0f:e1:25:c4:45:1a:a9:3e:
db:06:4f:5a:ca:af:57:b9:2f:19:0f:47:1d:0c:52:df:2d:03:
43:d1:c5:bc:f3:58:48:80:ce:26:96:51:19:f5:c0:d5:2a:1e:
34:e2:8c:35:37:58:1c:d6:74:56:1b:1f:2d:3d:c5:50:f3:81:
89:fa:72:0b:40:ce:4c:a9:65:b9:58:f5:f4:fc:cb:a3:7a:0d:
d9:fb:e2:b0:1a:ce:33:25:32:1e:01:e6:2d:52:05:46:c6:cc:
0f:f6:67:40:15:da:d4:e2:06:a0:07:51:3b:f8:c6:59:73:24:
44:a7:9d:ea:86:8b:c4:dd:00:0b:6c:da:1b:e6:e2:4d:a9:8a:
2f:17:a8:31:0e:86:55:7b:e0:3f:bb:8a:0b:0b:d3:9f:f1:56:
86:e4:0b:f9:db:0b:da:a3:4c:a2:28:5c:29:21:dc:bb:eb:38:
9e:ca:84:d9:76:e6:0f:82
De-Installation¶
Removing the certificate is similar process to installing it. To remove the certificate from the system, remove the package using zypper or YaST and then reboot the system. At the system console the following UEFI prompt will be displayed:
Shim UEFI key management
Continue Boot
_ Delete MOK
Enroll key from disk
Enroll hash from disk
Move cursor to Delete MOK and hit Enter
[Delete MOK]
Input the key number to show the details of the key or
type '0' to continue
1 keys(s) in the key list
Type 1 Enter to view the key details and after confirming that the details match the key to be deleted, type 0 Enter
Delete the key(s)? (y/n):
Type y Enter to delete…
Password: _
Enter the root password of the SUSE Linux Enterprise OS that the Secure Boot certificate package was removed from.
Press a key to reboot system
Now the key should be removed from the MOK database.
MOK Blacklist (MOKx)¶
Note: The MOK Blacklist functionality is only supported in SUSE Linux Enterprise Server/Desktop 12 and later.
The MOK blacklist allows the user to forbid particular kernel modules from being loaded as identified by the public key of the module signature.
The usage of MOK blacklist is similar to MOK. Just add --mokx or
-X to indicate that it’s a MOK blacklist request.
To add a key:
Create the request with mokutil and type a password (or use the root password with “-P”)
# mokutil -X --import <key>
Reboot the system and enter the MokManger UI. Select
Enroll MOKXand type the password. MokManager will reboot the system again.Boot the system and check the MOK blacklist with mokutil
# mokutil -X --list-enrolled